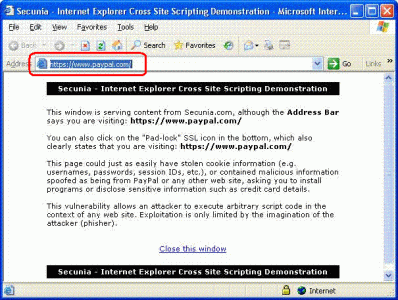
Most of us are constantly aware of the security holes appearing (and sometimes re-appearing) in Internet Explorer, and the endless stream of patches that fix them. And usually the description on Windows Update is vague like "allows code to be run that can be exploited by malicious people".  But we never see what the hole really looks like or how it could be exploited.
But we never see what the hole really looks like or how it could be exploited.
Here's something different: here's an example of a current exploit that could be used to conduct cross-site scripting attacks. Check it out for yourselves in IE6 and see for yourselves:
<B> http://secunia.com/internet_explorer_cross-site_scripting_vulnerability_test/ </B>
Note: This is safe and does not contain viruses, trojan, keyloggers or any other spooky stuff.
Ok... let's have a poll who's going to continue using IE after reading this post?
Here's something different: here's an example of a current exploit that could be used to conduct cross-site scripting attacks. Check it out for yourselves in IE6 and see for yourselves:
<B> http://secunia.com/internet_explorer_cross-site_scripting_vulnerability_test/ </B>
Note: This is safe and does not contain viruses, trojan, keyloggers or any other spooky stuff.
Ok... let's have a poll who's going to continue using IE after reading this post?